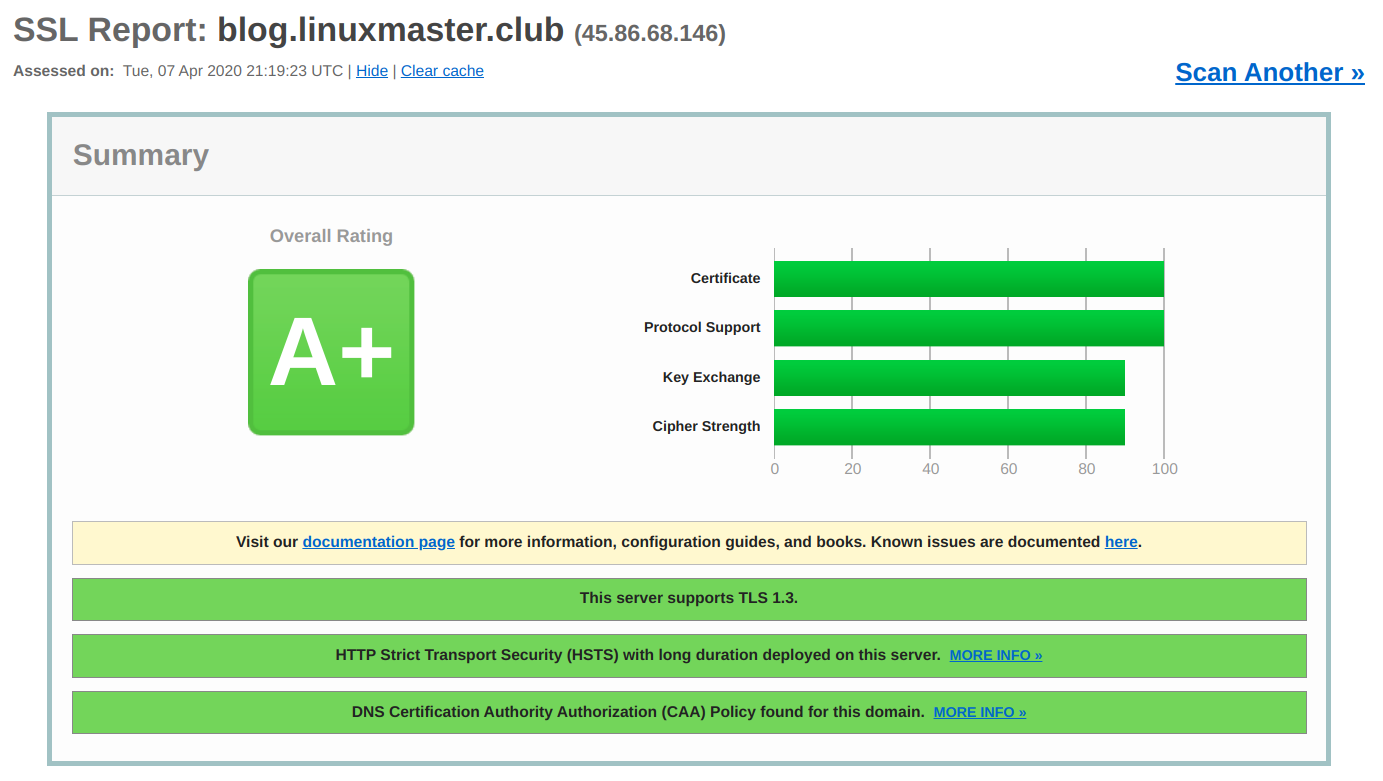
Great A+ SSL Security on nginx
Configure SSL Protocols:
ssl_protocols TLSv1.2 TLSv1.3; # TLSv1.3 requires nginx >= 1.13.0Note: All protocols other than TLS 1.2 and TLS 1.3 are considered unsafe.
The cipher suites that provide great forward secrecy:
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384;If backwards compatibility is important for you, here is alternative:
ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:ECDHE-RSA-AES128-GCM-SHA256:AES256+EECDH:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";Use strong Diffie Hellman parametar (4k):
ssl_dhparam /etc/nginx/ssl/dhparam.pem;
ssl_ecdh_curve secp384r1; Create strong Diffie Hellman parameters:
openssl dhparam -out /etc/nginx/ssl/dhparam.pem 4096Add HSTS header (required for A+):
add_header Strict-Transport-Security "max-age=31536000";Make sure you also add these lines:
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;Check nginx configuration and restart nginx:
nginx -t
service nginx restart